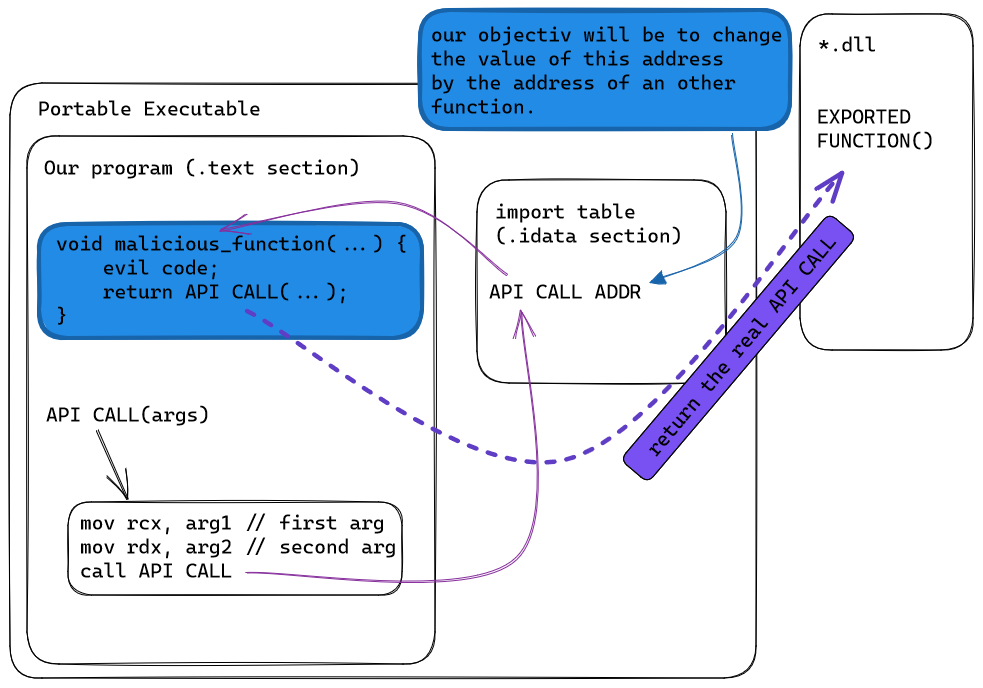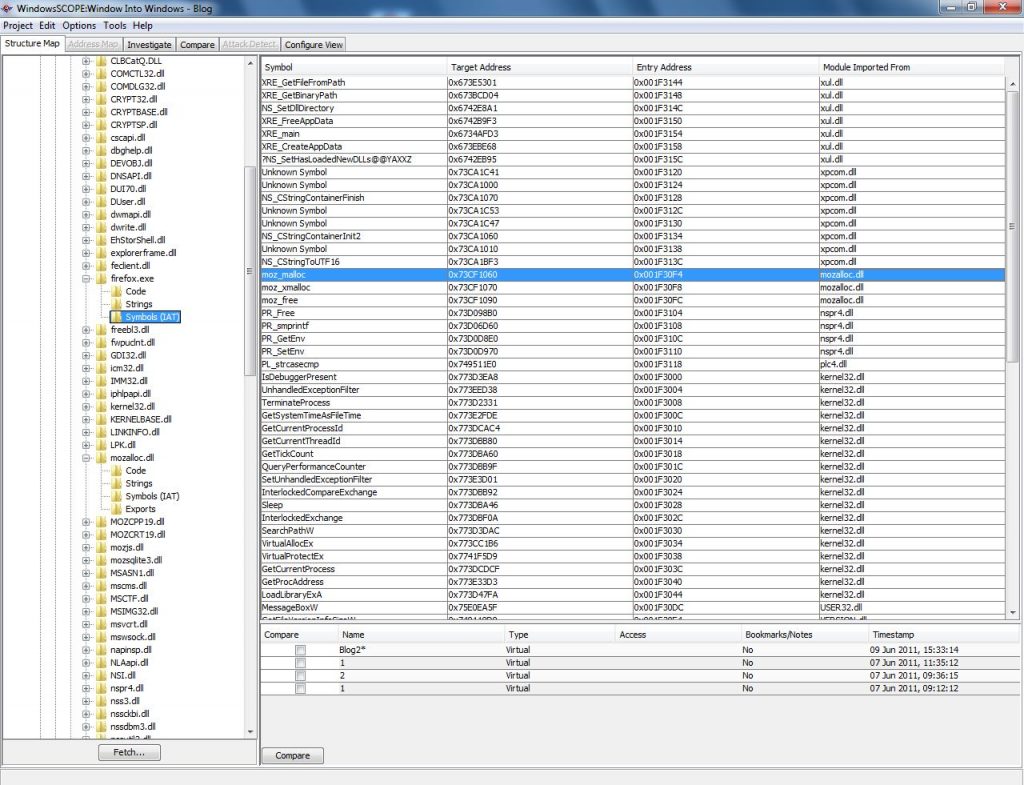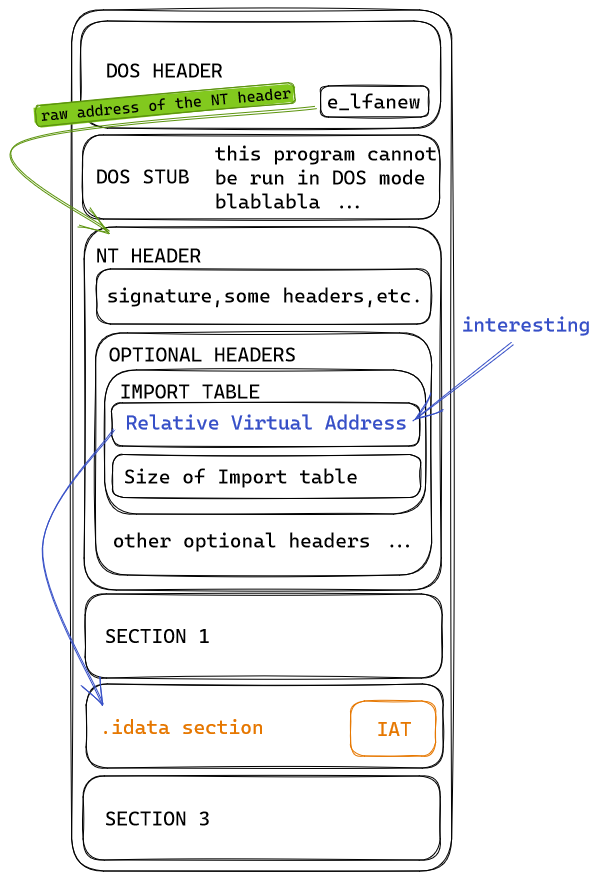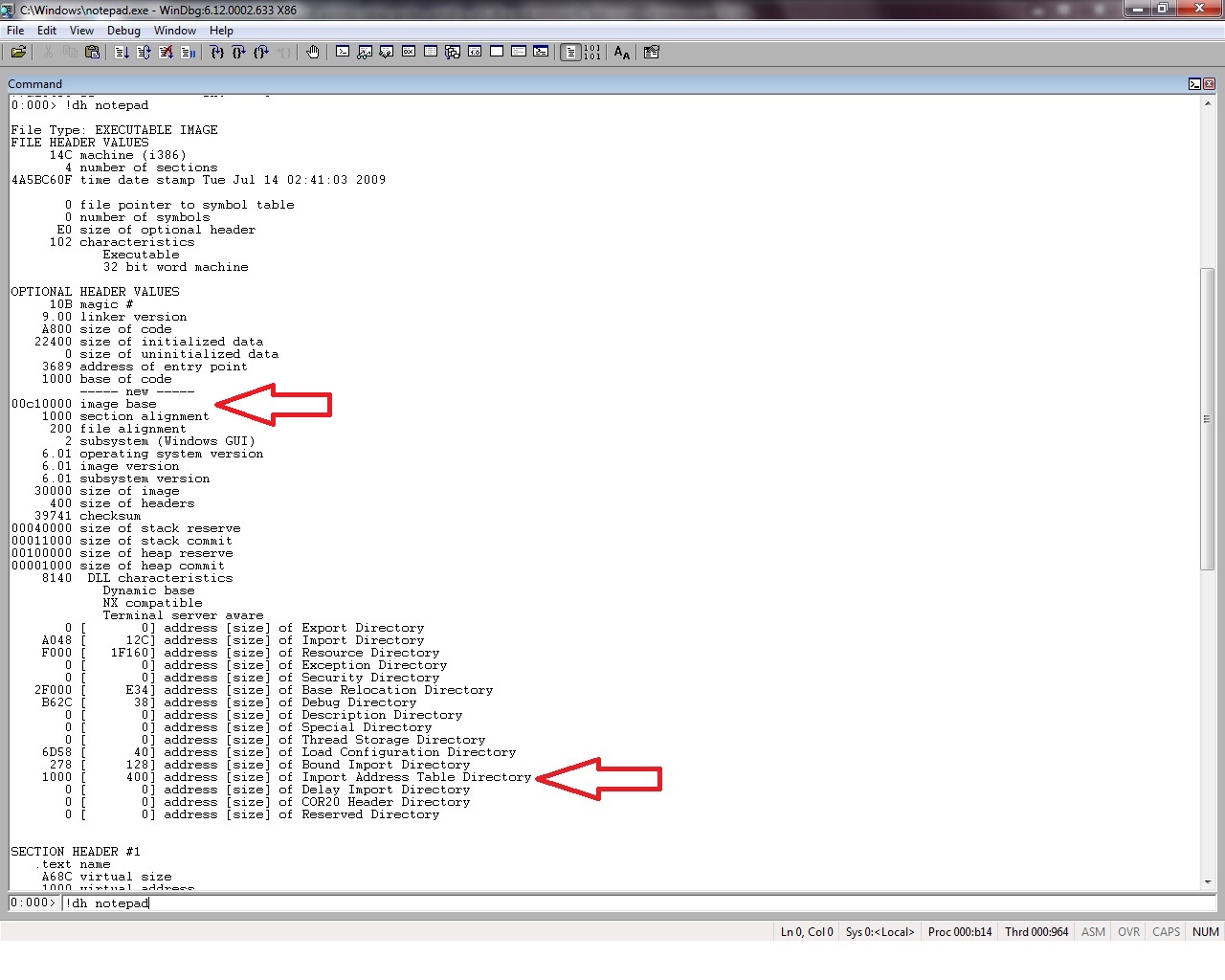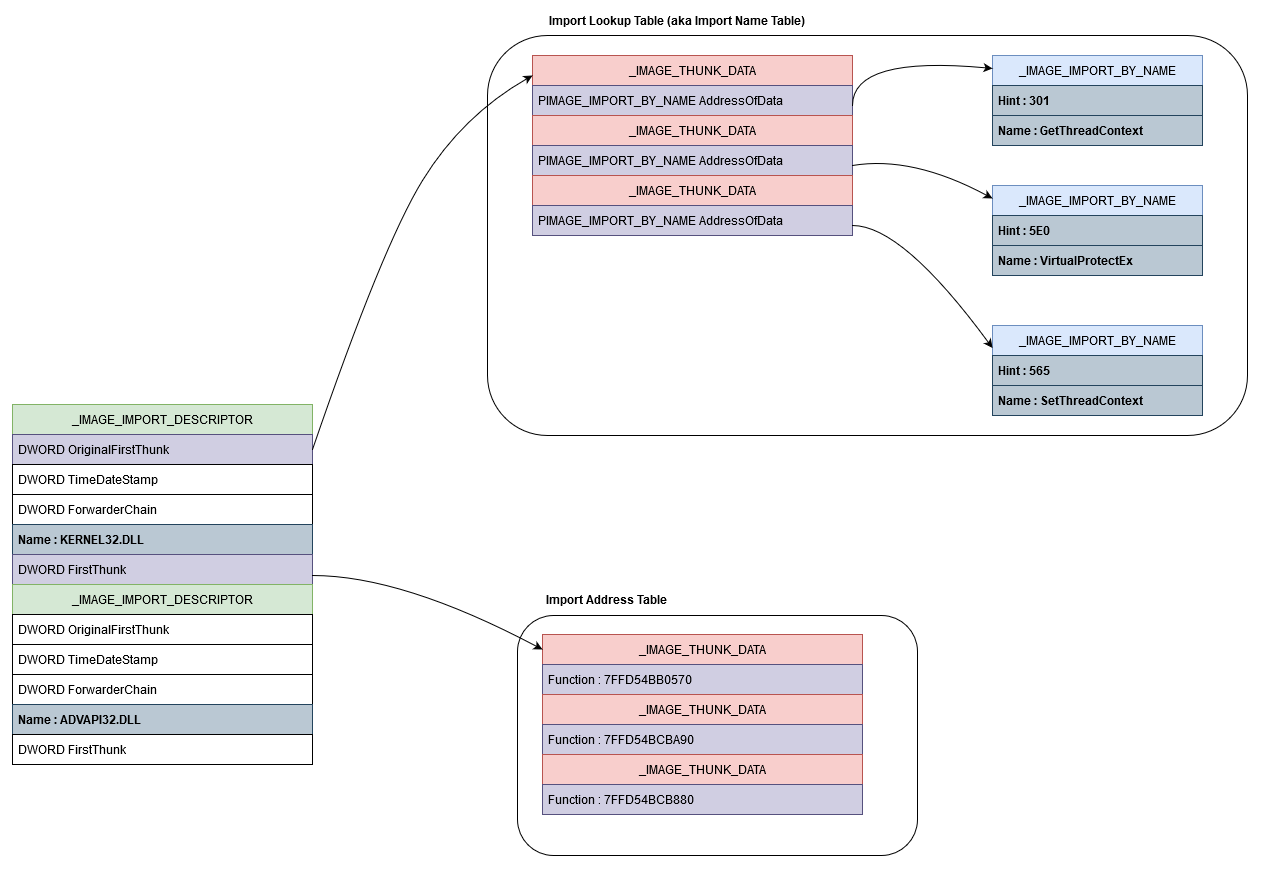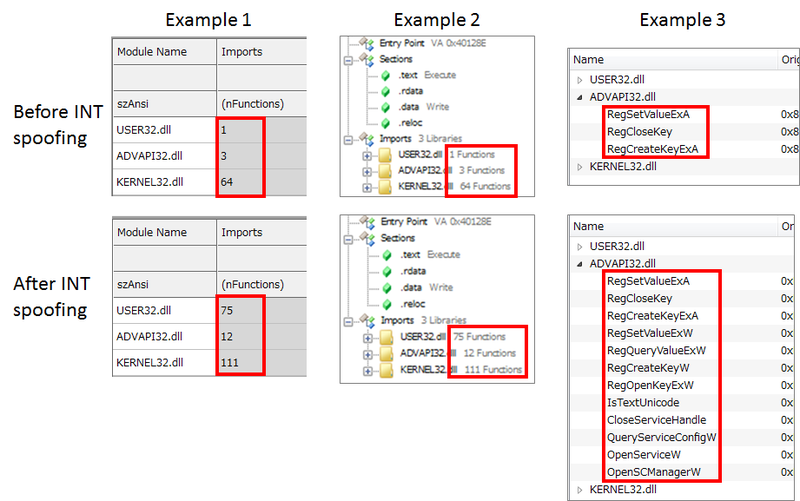
Anti-analysis technique for PE Analysis Tools –INT Spoofing– - JPCERT/CC Eyes | JPCERT Coordination Center official Blog

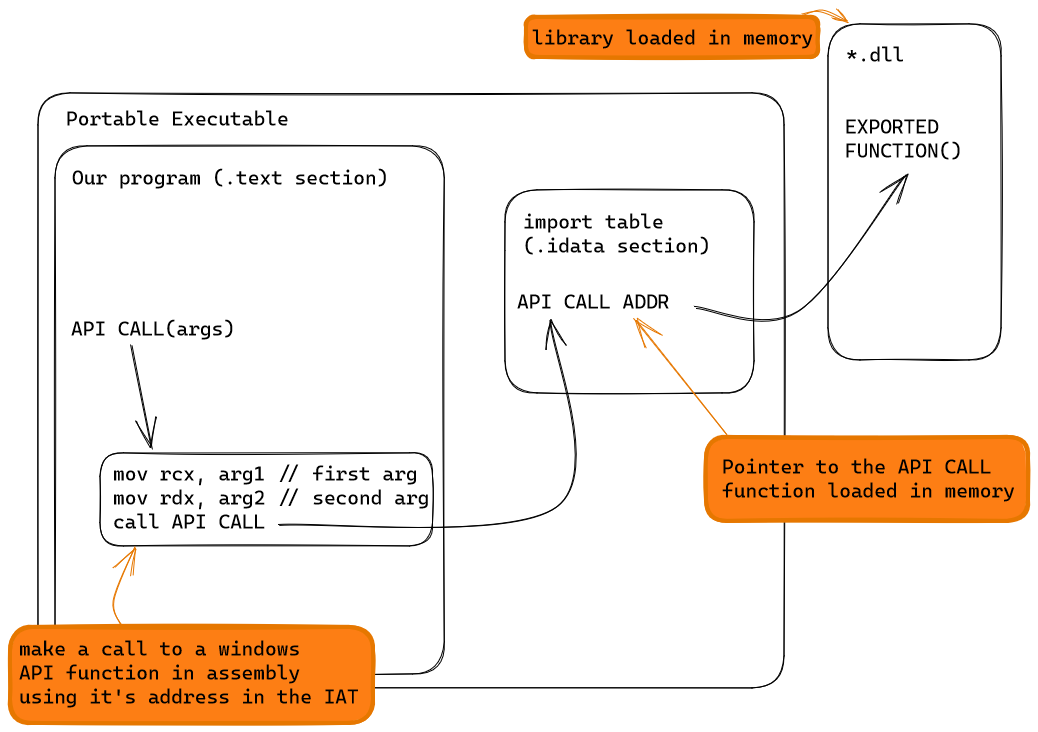
API Hooking Method. First, the executable calls an API, API2, described... | Download Scientific Diagram

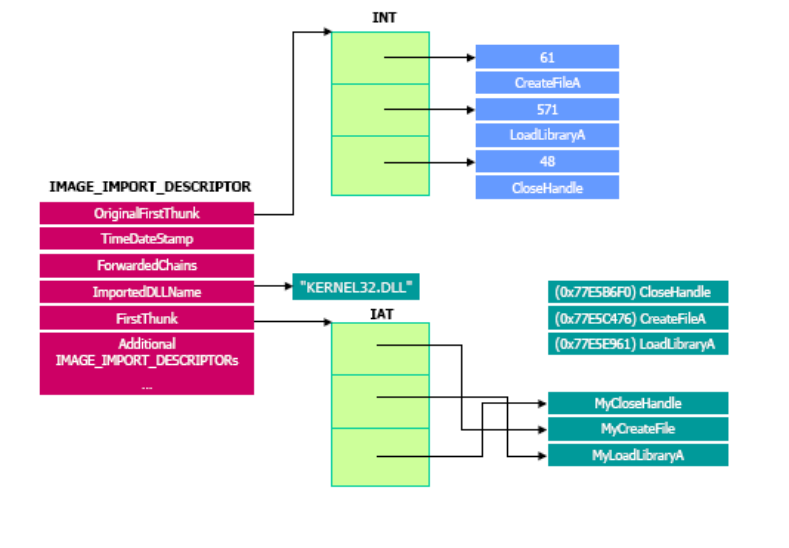
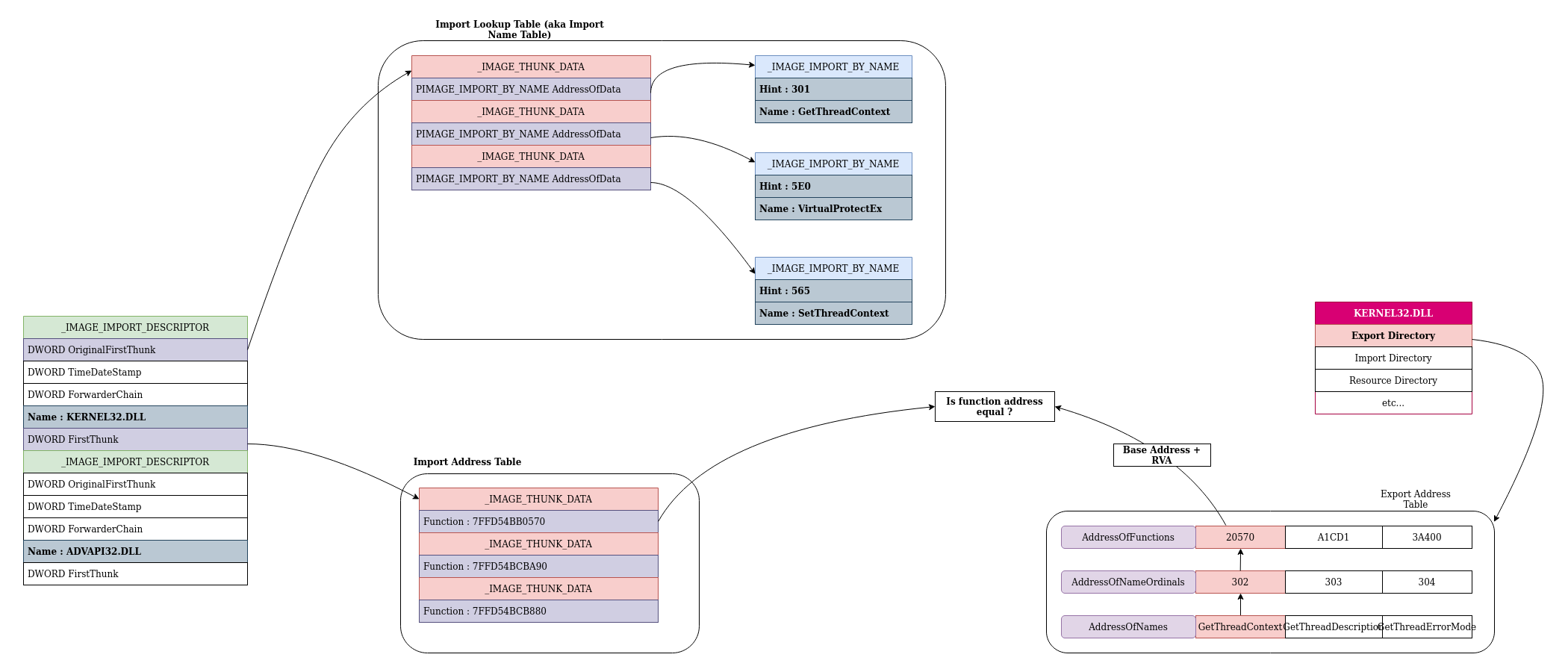
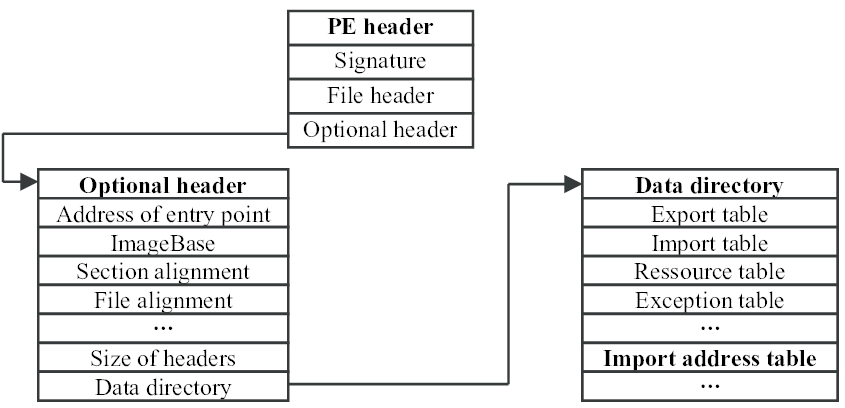
winapi - What's the difference between the import table, import adress table, and import name table? - Stack Overflow






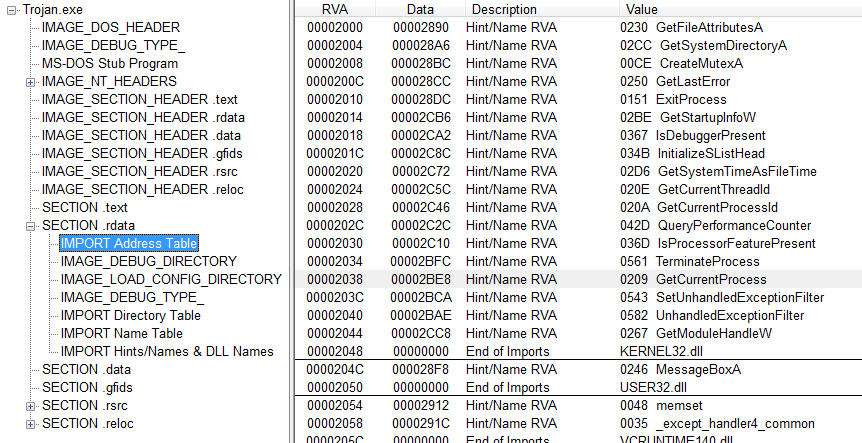
![Information] Beginner Introduction - IMPORT ADDRESS TABLE Information] Beginner Introduction - IMPORT ADDRESS TABLE](https://i.imgur.com/1kSkra9.png)